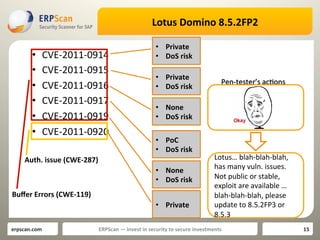
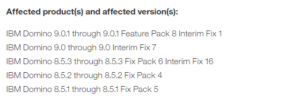
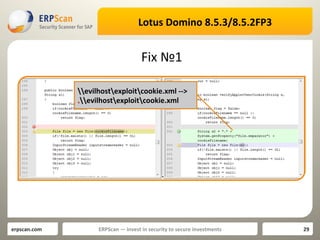
![SOLVED] Lotus Domino iNotes SSL uses an unsupported protocol. ERR_SSL_VERSION_OR_CIPHER - Team Collaboration SOLVED] Lotus Domino iNotes SSL uses an unsupported protocol. ERR_SSL_VERSION_OR_CIPHER - Team Collaboration](https://content.spiceworksstatic.com/service.community/p/post_images/0000359999/5d00794b/attached_image/ssl.png)
SOLVED] Lotus Domino iNotes SSL uses an unsupported protocol. ERR_SSL_VERSION_OR_CIPHER - Team Collaboration
CVE-2005-2428-IBM-Lotus-Domino-R8-Password-Hash-Extraction-Exploit/exploit.py at master · schwankner/CVE-2005-2428-IBM-Lotus-Domino -R8-Password-Hash-Extraction-Exploit · GitHub
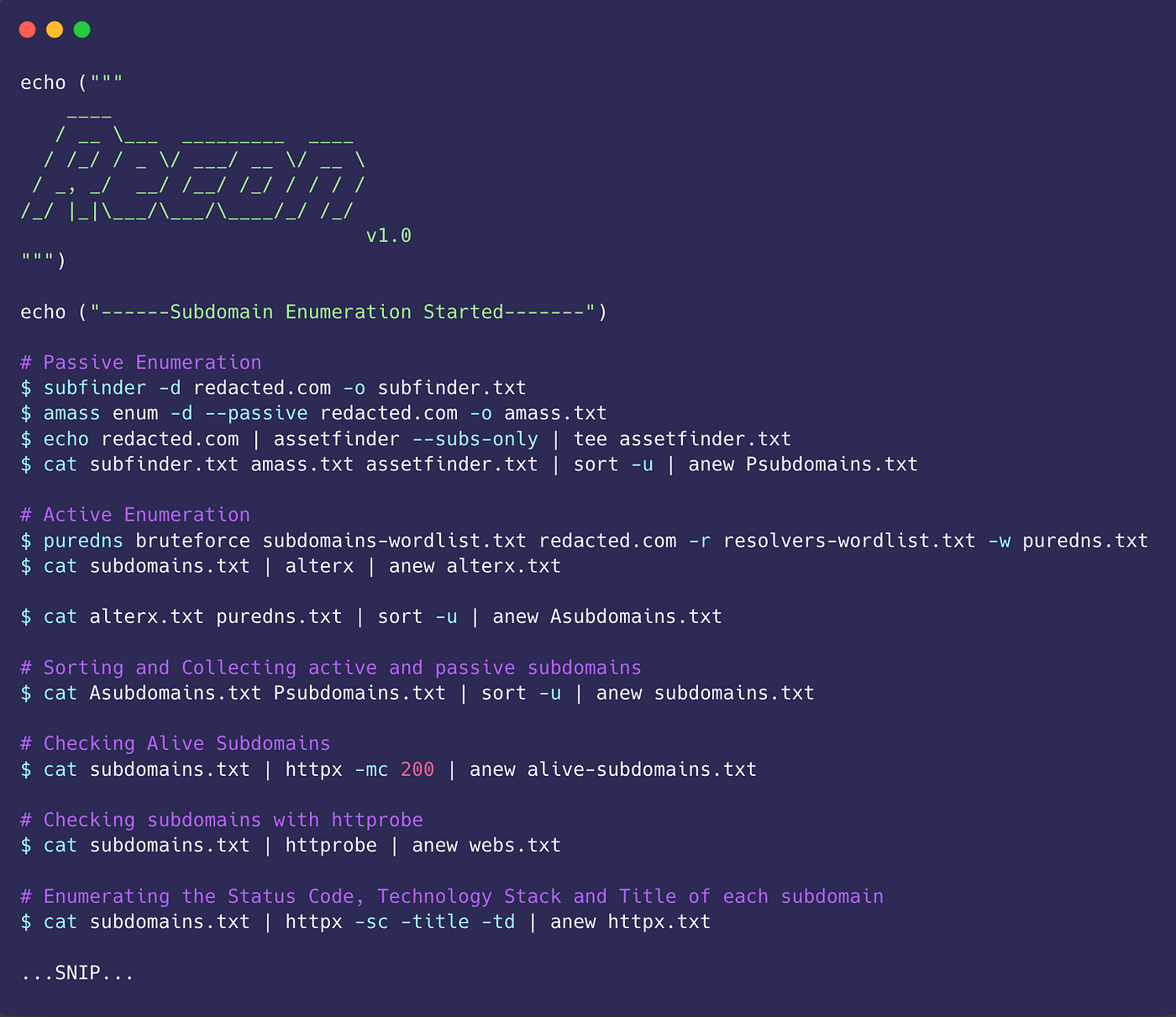
How a misconfigured Lotus Domino Server can lead to Disclosure of PII Data of Employees, Configuration Details about the Active Directory, etc | by Aayush Vishnoi | Medium

How a misconfigured Lotus Domino Server can lead to Disclosure of PII Data of Employees, Configuration Details about the Active Directory, etc | by Aayush Vishnoi | Medium

How a misconfigured Lotus Domino Server can lead to Disclosure of PII Data of Employees, Configuration Details about the Active Directory, etc | by Aayush Vishnoi | Medium

Ibm Lotus Domino Designer 6 Application Development With Lotus Domino Designer | PDF | Ibm Notes | Databases