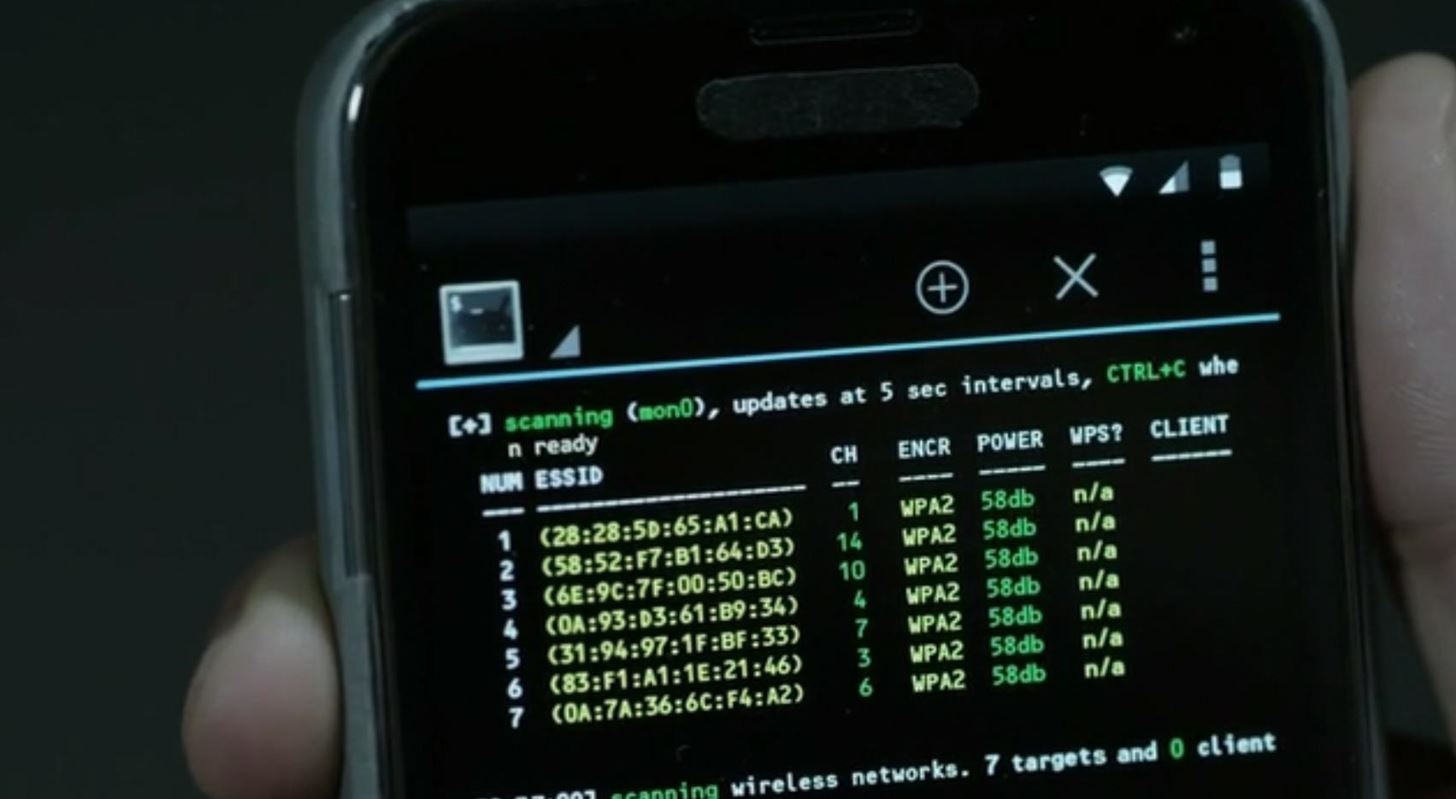
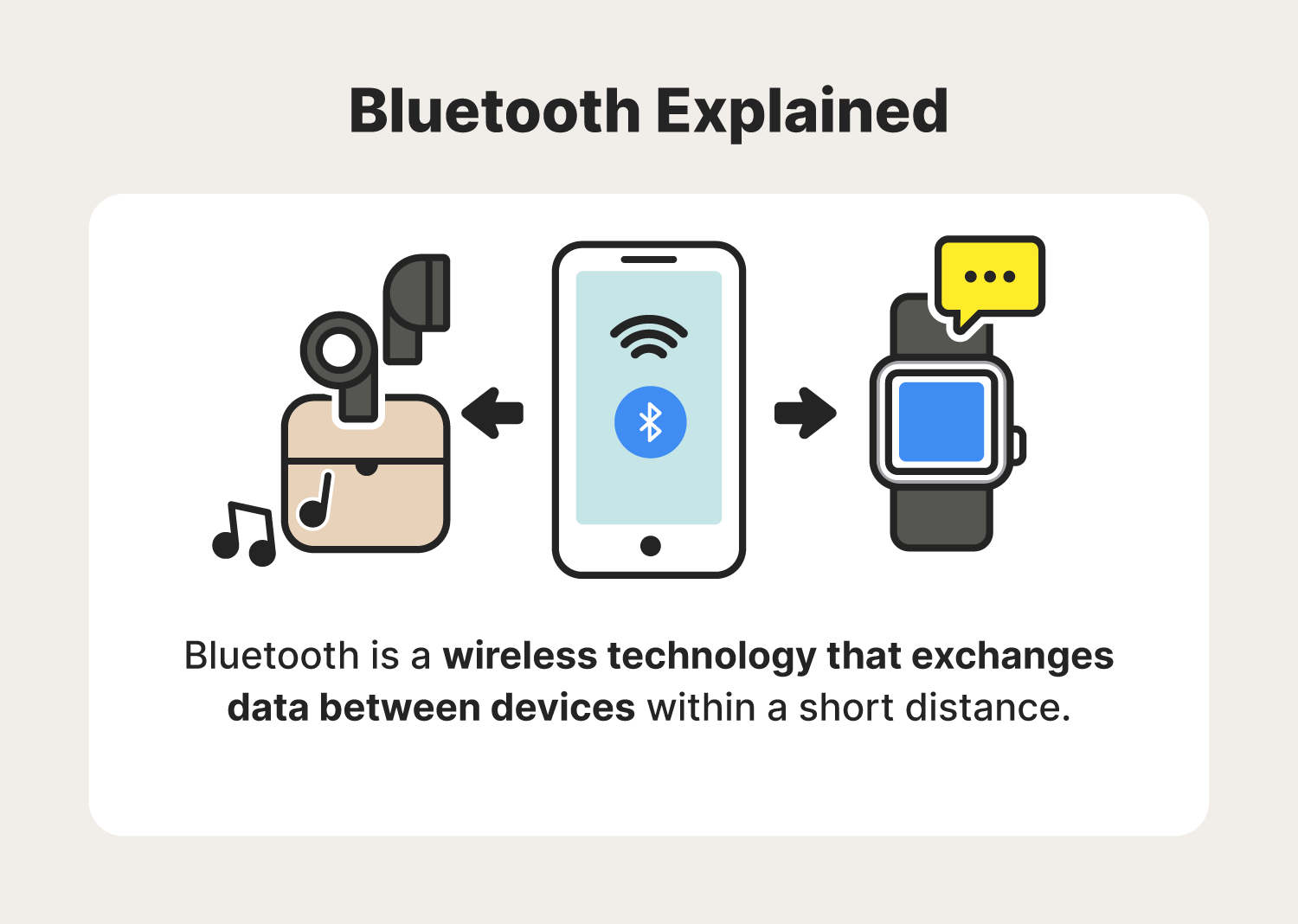
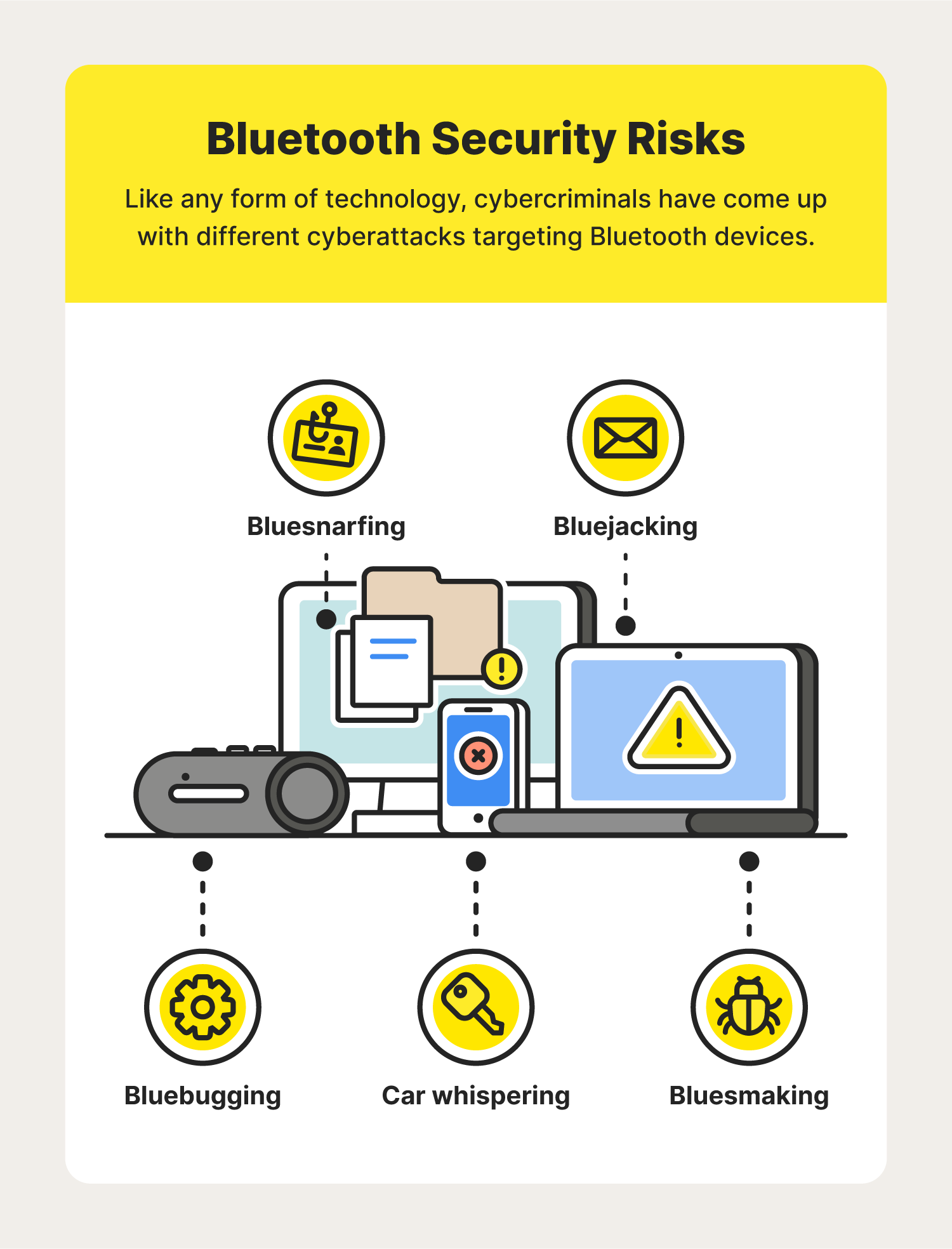
Keep Bluetooth, Wi-Fi off, do an app 'audit': How to keep your smartphone safe & secure from hackers - The Economic Times

Amazon.com: USB Defender | Data Blocker | Blocks Unwanted Data Transfers | Protects Smartphone & Tablets From Public Charging Stations | Hack Proof, 100% Guaranteed : Electronics






/Hacked-phone.png?width=1319&name=Hacked-phone.png)